For two hours yesterday, April 24th, 2018, hackers diverted visitors of MyEtherWallet.com, accessing user accounts and stealing approximately 215 ether.
MyEtherWallet warned users on Reddit and Twitter as soon as the hack was identified. But, this left a couple of hours where users of the wallet attempting to visit the MyEtherWallet.com website were redirected to a “spoof” or phishing site controlled by the hackers.
The hack employed the “decade-old” technique of redirecting Domain Name Servers (DNS) rather than a hack to, or weakness in, MyEtherWallet.
The wallet was quick to point out that this kind of hack can happen to any major website, including large banks, and was not due to a lack of security on the part of the MyEtherWallet platform.
The hackers exploited well known internet vulnerabilities in public facing DNS servers including Google DNS and Amazon DNS servers for MyEtherWallet. A DNS directs users who type in a web address to the relevant web server. The hackers were able to hijack this routing and redirect internet traffic away from the MyEtherWallet.com site.
BGP hijack this morning affected Amazon DNS. eNet (AS10297) of Columbus, OH announced the following more-specifics of Amazon routes from 11:05 to 13:03 UTC today:
205.251.192.0/24
205.251.193.0/24
205.251.195.0/24
205.251.197.0/24
205.251.199.0/24— InternetIntelligence (@InternetIntel) 24 April 2018
According to Cisco:
“DNS looks up and resolves domains, like google.com, to their correct IP addresses, which are the real destination.”
Affected users would have received an SSL warning when were routed to the spoof or fake version of the MyEtherWallet website and would have needed to click “ignore” to eventually arrive at the hacker’s website, reportedly in Russia.
The SSL warning may have looked something like this:
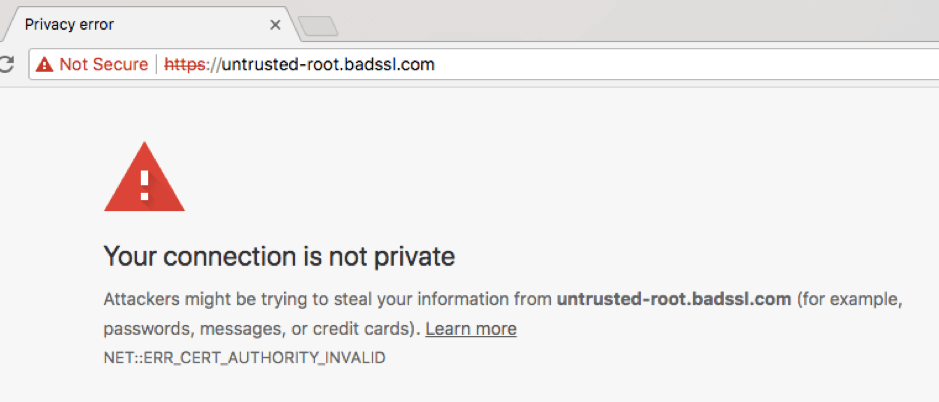
It’s a key example of why red SSL warnings should never be ignored. MyEtherWallet warned users:
“PLEASE ENSURE there is a green bar SSL certificate that says “MyEtherWallet Inc” before using MEW.”
Users were advised to run a local offline copy of their wallets, and to use Cloudflare DNS servers rather than Google while the hack continued.
“In the meantime we urge users to ignore any tweets, reddit posts, or messages of any kind which claim to be giving away or reimbursing ETH on behalf of MEW.”
MyEtherWallet later shared a technical breakdown of the hack:
Complete technical breakdown on what happened today by @Cloudflare https://t.co/Qu8grqx6jC
— MyEtherWallet.com (@myetherwallet) April 24, 2018
It was quickly identified that over 150k worth of ETH had been stolen in the DNS hack with 179 transactions totalling 216.06 ETH sent to 0x1d50588C0aa11959A5c28831ce3DC5F1D3120d29. More Ethereum may have been stolen in the attack if hackers have managed to retain and re-use stolen MyEtherWallet user data.
Similar hacks affected Apple, Facebook, Google, and Microsoft in December 2017, and Stellar in January 2018, when $400,000 of Lumen was stolen.
The crypto-economy is a major target for hackers employing a range of techniques. Cryptocurrency users should make themselves aware of the potential signs of a hack or compromise of their data or systems and actively seek out ways to protect their investments. Hardware-based cryptocurrency wallets are recommended to protect against wallet or exchange hacks.
Blockchain operators, developers, and cryptocurrency related firms often work tremendously hard to protect users from hacks, but the nature of the internet dictates they may never be 100% successful in doing so.

