
In 2018, Kaspersky Lab recorded a 4-fold increase in cryptomining attacks in the Middle East, Turkey and Africa (META) region from 3.5 million in 2017 to 13 million this year, the firm said on December 14.
The increase in cryptomining attacks in META comes at a time when digital threats and cybercriminal activities in the region are on the rise. Banking malware attacks reached almost half a million, or a 17% increase, in 2018, according to the KSN statistics by Kaspersky Lab.
“The META region is becoming more appealing to cybercriminals, with financial and malicious cryptomining attacks taking center stage,” Fabio Assolini, senior security researcher at Kaspersky Lab, said in a statement.
“We discovered six new ATM malware families in 2018. On the other hand, illegal mining of cryptocurrencies has increased dramatically to overtake the main threat of the last few years: ransomware. We believe the reason behind this is that mining is silent and cause less impact that ransomware, making it less noticeable.”
2018 saw the global outbreak in malicious cryptocurrency mining, with the number of attacks increasing by more than 83%, with over five million users attacked online in the first three quarters of 2018, compared to 2.7 million over the same period in 2017, according Kaspersky Lab.
As the malicious use of cryptocurrency miners rose this year, ransomware attacks on the other hand decreased as attackers changed strategies, opting instead to perform discreet mining on infected devices rather than demand a ransom and attract attention.
In a report released last month, Kaspersky Lab researchers highlighted that the malicious use of cryptocurrency miners peaked in March with more than 1,169,000 attacks, before decreasing steadily as general interest in cryptocurrencies waned and prices declined.
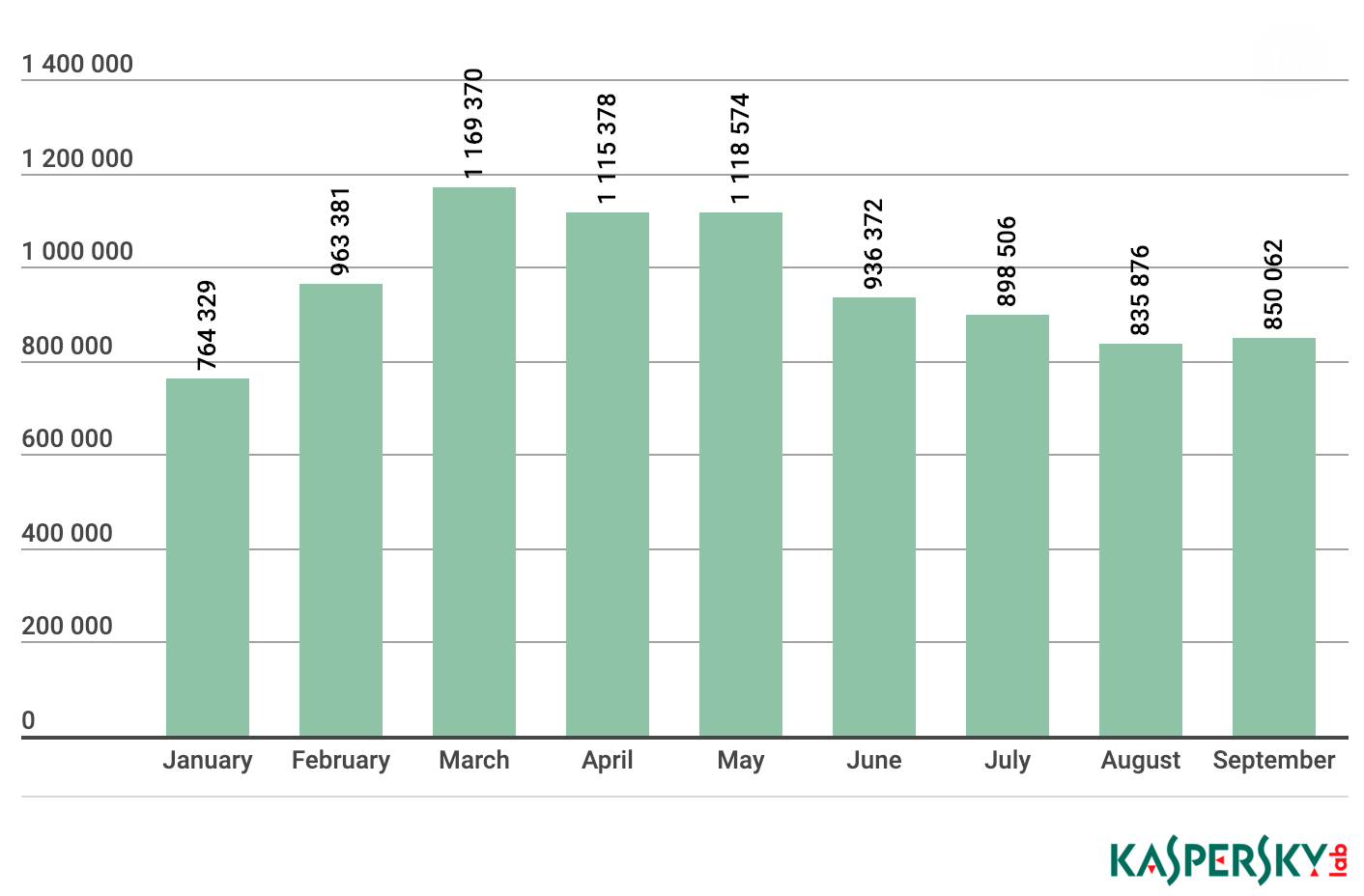
Hidden mining software was very popular among botnet owners, the research found. It also revealed that miners mainly infected devices by luring users into installing pirated software and unlicensed content.
“Our analysis of the economic background of malicious cryptomining and the reasons for its widespread presence in certain regions revealed a clear correlation,” said Evgeny Lopatin, security expert at Kaspersky Lab.
“The easier it is to distribute unlicensed software, the more incidents of malicious cryptominer activities were detected. In short, an activity not generally perceived as especially dangerous, the downloading and installation of dubious software, underpins what is arguably the biggest cyberthreat story of the year – malicious cryptomining.”
A cryptomining malware takes over a computer’s resources and use them for cryptocurrency mining without a user’s explicit permission. Cryptominers usually find their way onto user computers and corporate machines along with adware, hacked games, and other pirated content.
Unlike ransomware programs, which are noticeable right away, it might be quite a while before a victim of a cryptominer notices that 70–80% of their CPU or graphics card power is being used to generate cryptocurrencies.
According to separate Kaspersky Lab report, a single cryptocurrency mining botnet can net cybercriminals more than US$30,000 per month.
The most common cryptocurrency among all illegally mined cryptocurrencies is Monero (XMR), primarily due to its anonymous algorithm, relatively high market value, and ease of sale. Palo Alto Networks estimates that a total of US$175 million worth of Monero has been mined illegally, representing around 5% of all Monero currently in circulation.

