SEO tools provider and marketing data company Ahrefs analyzed 175 million websites in their database to find out exactly how many websites are crypto-mining using their visitor’s computers.
Cryptojacking is a growing issue for website owners and organizations globally, with many falling victim to cryptocurrency mining malware hacks. These hacks install mining scripts into websites allowing hackers to mine cryptocurrencies unbeknown to website visitors and owners.
Crypto-mining scripts can use website visitor’s computer systems, central processing units (CPUs), graphics processing units (GPUs) and their electricity, sending mining rewards to hackers at hidden cryptocurrency wallet addresses.
Website owners may also knowingly operate cryptocurrency mining scripts, but without warning visitors, using visitor’s computer power to mine cryptocurrencies for their own benefit.
In both cases, website visitors are not aware their systems are being used in this way unless they happen to notice their systems slow down or spot hikes in processor or browser activity.
Ahrefs crawled the 175 million websites in its database, including subdomains, with an application called Wappalyzer which reveals the technologies a website employs. Wappalyzer is able to identify 14 common crypto-mining scripts.
A total of 23,872 unique website domains out of the 175 million analyzed were found to be running cryptocurrency mining scripts. Of the total identified, most of them, at 93.82%, were running the Coinhive crypto-mining script.
Ahrefs went on to analyse how many visitors these sites are likely receiving via organic search from Google, most of which would be unaware they are mining cryptocurrency for hackers or site owners while they are browsing the site. Ahrefs estimated monthly search traffic based on search volumes and estimated click-through rates. They summarised that roughly 91% of websites with cryptocurrency mining scripts installed were getting less that 50 visitors via Google each month.
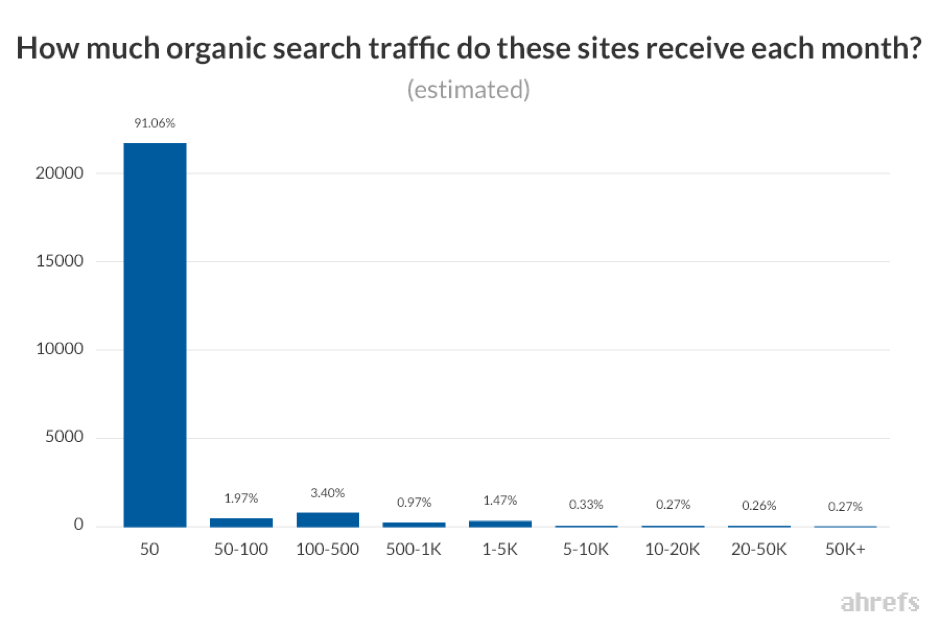
There are several reasons for traffic to these sites being low, the first is that hackers could be targeting abandoned, unattended websites with open vulnerabilities. The second is that high profile websites are both better protected and are unlikely to risk losing valuable visitors and reputation by knowingly operating crypto-mining programs. It has also been rumoured that Google Chrome blocks websites running crypto-mining scripts.
Finally, larger, more popular sites are likely to achieve a higher CPM for advertising and thus the incentives for running malware are less than they’d receive from conventional advertising.
Most of the websites identified also fell outside of Ahrefs’ top 100,000 domains according to the Ahref Domain Rating system. The Domain Rating system grades the popularity of a website based on the amount and quality of inbound links it has from other websites.
The 175 million websites analysed included subdomains. Of the 23,872-total found with crypto-mining scripts, 1,308 were subdomains. 1,257 out of the 1,308 were subdomains published on Google’s blogging platform, blogspot.com.
Ahrefs compared its results to those from a similar investigation by Troy Mursch of Bad Packets Report. The Bad Packets Report used data from the publicWWW database so included 17.5% more sites and only checked for 5 common crypto-mining scripts, including Coinhive.
The Bad Packets Report found 43,000 websites running crypto-mining scripts. The difference is, in part, attributed to PublicWWW being a historic database and including more inactive websites.
The conclusion from the study by Ahrefs is that an estimated 1 in 7,353 websites are running crypto-mining scripts, many of these being older sites with fewer visitors. Thus cryptojacking, or at least unwitting crypto-mining for the benefit of others, is possibly not as widespread as some assume.
That said, those that are affected and unwittingly mine cryptocurrencies may have seen a little extra wear and tear to their computer systems and a possible increase in their electricity bill.
Browser and website cryptojacking is not usually identified by antivirus or operating system protection. Users may or may not notice sudden spikes in CPU or GPU usage or activity surges in applications like Chrome Task Manager.
To fully protect systems and browsers, browser plugins such as minerBlock and No Coin are available which block crypto-mining scripts.

